A guide to business email encryption: methods, standards, and solutions
Understand your encryption options for secure business comms
Understand your encryption options for secure business comms

Email encryption encodes emails during transmission. It safeguards email content, which often includes sensitive or private data, by making them indecipherable to all but the intended recipient or recipients. Anyone who opens the email without permission sees only a jumble of letters, reducing the risk of exploitation by cybercriminals.
Concealing information with a cypher dates all the way back to 60 BCE. Julius Caesar encoded messages by moving letters of the alphabet by three places. Cryptography has evolved in the millennia and is widely relied on in computing to facilitate:
Email encryption uses code to scramble messages, called plaintext, into illegible codes, called ciphertext. To decipher the message, you need to unlock the encrypted data with a decryption key that reverses the scramble.

Email encryption should be practiced as routinely and subconsciously as brushing your teeth. There’s almost always going to be a requirement to share some private information or personal data via email. This could relate to:
So, it’s in your interests to protect your communications from falling into the wrong hands. Implementing business email encryption comes with many upsides, including:
Helps you to meet legal requirements like GDPR, HIPAA, NIS2, and DORA by securing email communications.
Blocks a route cybercriminals take to access systems and data, reducing the risk of associated damages.
Demonstrating safe and secure operations reassures existing and potential customers, stakeholders, and employees.
Send and receive secure communications across different networks so you can embrace modern ways of working.
You might be familiar with the padlock icon synonymous with TLS in secure web browsing sessions, but it’s used in far more applications – including email. It provides security by encrypting the connection – not the message itself – between two points, e.g. browsers or servers, during data transmission.
Email TLS encryption establishes a secure connection through a process called a "handshake." During the handshake, the two communicating sides verify their identity, and generate encryption keys using asymmetric cryptography prior to exchange. Then, they use symmetric encryption to protect the data during the exchange. At the end of the session, the key is discarded.
The advantage of asymmetric cryptography is that you can share encryption keys securely over an insecure channel. But this requires much larger key sizes – 2048-bit keys are preferred for strong security. This makes the process slower than symmetric encryption, which uses smaller, faster keys for equivalent security strength.
S/MIME is a certificate-based protocol that allows you to send encrypted and digitally signed email messages, ensuring the confidentiality and authenticity of every communication.
It operates on a public key infrastructure (PKI), which uses two cryptographic keys – a public key for encryption and private key for decryption. All participants in a data transaction must maintain their own private keys while sharing public keys with others. If a private key is compromised, a new key is needed to restore secure communication.
S/MIME uses digital certificates that are issued and verified by trusted third parties known as certificate authorities. The certificates hold essential information to establish the validity of the public key. When an email is sent, a digital signature is applied to assure the recipient it was sent by a verified sender and content wasn’t altered during transmission. If any changes are made to an email after it’s signed, the signature becomes invalid.
A nineties baby, PGP was one of the first free cryptographic solutions. It’s still widely used for end-to-end encryption and is particularly useful for exchanging highly sensitive data.
It works by combining data compression, symmetric and asymmetric key cryptography, and hashing. When you send a message, PGP generates a random session key to encrypt the message with symmetric encryption. The recipient can decrypt the session key with their private key and read the original message.
Encryption standards, also known as encryption algorithms, are a measure of the strength of the lock securing your data. The following are the most common in modern cryptography:
AES uses symmetric encryption. It’s generally regarded as one of the most secure encryption standards because of its 256-bit key length. It’s also generally faster and more resistant to brute-force attacks than other encryption standards which is why it’s trusted by governments and global enterprises to protect sensitive data.
RSA uses asymmetric encryption, with public key for encryption and a private key for decryption. It shares public keys openly so users can encode messages without sharing a key each time. People typically use it for encrypting digital signatures rather than files or messages as it uses more processing power than symmetric encryption.
Unlike AES and RSA, it's impossible to decrypt SHA. By design, it converts data into strings of letters and numbers – or hash values – that can’t be reversed. It’s encryption-adjacent, because people use it to authenticate messages and data, keeping them safe at rest.
Rather than encrypting data, DSA generates digital signatures and verifies identities to ensure messages aren’t tampered with during transmission. People often use it alongside other standards like SHA and AES.
If you see Data Encryption Standard (DES) anywhere, be wary. It was once widely used, but the keys are only 56-bit, so is now considered insecure.
If you’re researching email encryption software, these are your broad options.
Free, open-source encryption software works for some, but there are of course limitations. Some operate subscription models with storage or file size restrictions, for example.
Although open-source software isn’t necessarily less secure than proprietary software, it takes a lot of maintenance. If you want to go down that route, thoroughly research the development process to ensure vulnerabilities and patches are dealt with quickly to ensure a good level of security.
Many email providers offer built-in encryption solutions. Naturally, there are limitations to these, so do your research before deciding if a ready-made solution is right for your business email encryption.
Taking Outlook and Gmail as examples, this is what you can expect.
Gmail uses TLS to encrypt the connection when messages travel between email servers. This provides protection in transit but doesn’t encrypt the email itself. To keep the connection safe, both parties must use an email delivery service that supports TLS.

You can encrypt messages via a dropdown menu when writing emails. Outlook’s encryption works with external email providers, but you have to rely on the sender knowing what to encrypt, and remembering to encrypt before sending.

For something more advanced and bespoke, go for a specialist solution. Usually, these providers will consult with you to carry out a needs assessment before recommending the best approach. They’ll offer powerful features – for example, some solutions read and analyse data, adapting security levels based on what’s being sent.
Take Zivver as an example. Our secure email solution provides:
You may or may not need this kind of solution, but it’s good to explore your options so you can make an informed decision.
We considered Zivver alongside an alternative email security solution and, while the other option was okay, we were blown away by Zivver…We had a meeting with Zivver and were not only impressed by the solution itself, but with the team’s responsiveness and communication. The product demo was clear and the team made an effort to understand our priorities and challenges. We proceeded with Zivver and haven’t looked back!”



Zivver is the email security solution that prevents data loss and supports compliance in Microsoft 365, Outlook and Gmail.
Adaptable, user-friendly, and powered by contextual machine learning, Zivver integrates with email clients to stop the leading causes of data leaks. Our suite of email security tools empower users to share sensitive data by email safely and with confidence, with unparalleled encryption and human error prevention tools.
Secure email. Effortless compliance.

12 min read
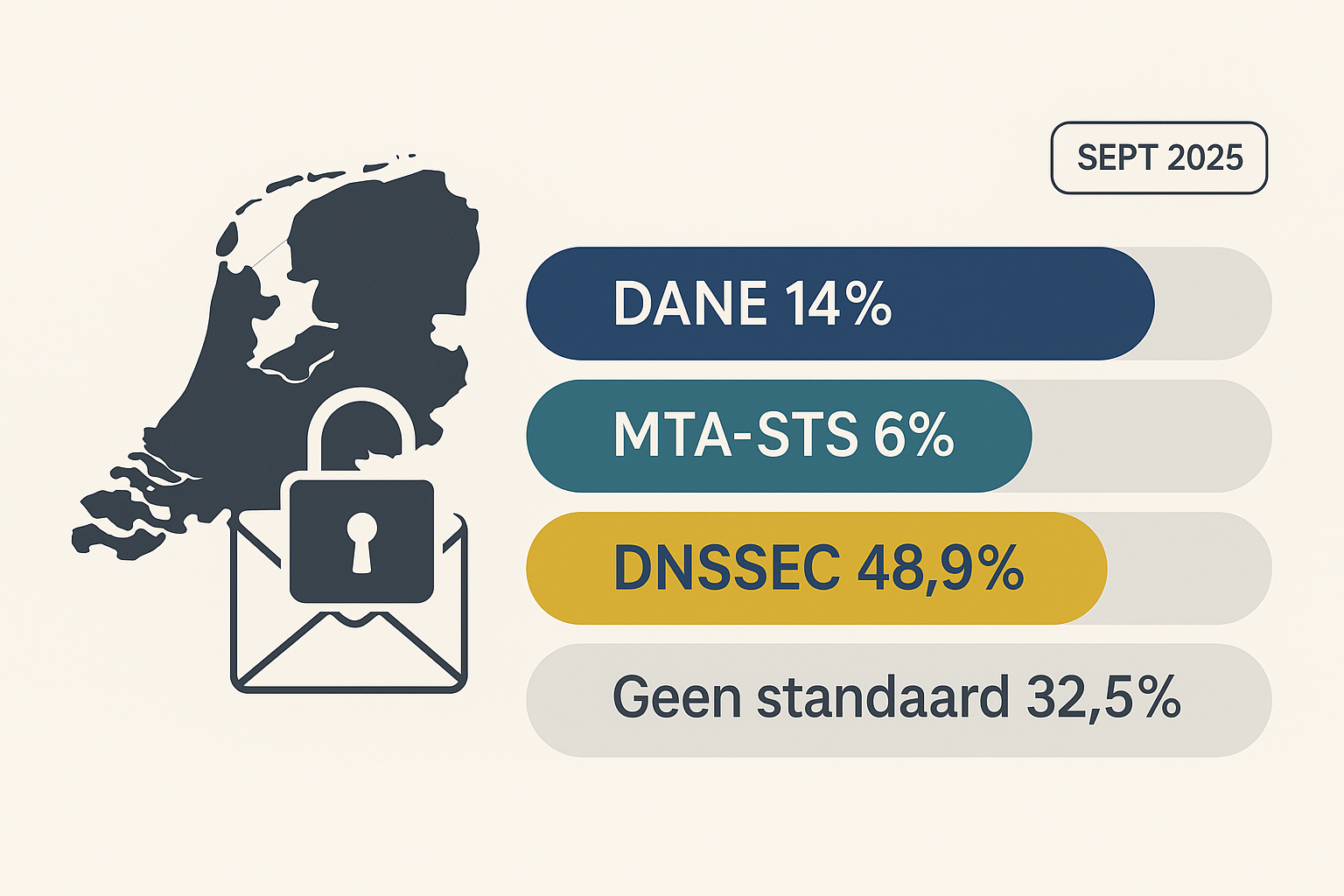
Summary Only 14% of the domains analyzed support DANE, and just 6% support MTA-STS. This means that over 80% of domains still fail to meet the basic standard for secure email transport. One in three d...

min read
Learn how email data loss prevention keeps sensitive information safe.

min read
Hear insights from AI and cybersecurity leaders on how to build cyber resilience through AI powered tools and training.