Zero-knowledge encryption to protect sensitive emails
Only the best-in-class encryption is robust enough for sensitive emails and files.
Only the best-in-class encryption is robust enough for sensitive emails and files.


Email was never designed to be secure. Prevent the leading causes of data loss and email with total confidence by enhancing Outlook, M365, or Gmail with integrated zero-access encryption.
Zivver uses best-practice standards during transmission (TLS 1.3, or otherwise TLS 1.2 with approved cipher suites). This is the same technology used by government applications and banks. This ensures that your data is securely sent to our protected platform for analysis of viruses, human errors, and potential data breaches.
Every Zivver email—even those sent by guest users—is stored with strong encryption. Zivver does not have the keys to decrypt the emails and files; only the sender and recipient do. A unique key is used for each conversation.


Most file transfer solutions do not meet compliance requirements and are inconvenient to use for both senders and recipients.
With Zivver, you can attach large files up to 5 TB directly from your mailbox. Contracts, PII, patient data—whatever you need to share, send it securely via email with zero-knowledge encryption.
Zivver provides legally verifiable Proof of Delivery, enabling you to keep track of the status of emails. Apply 2FA and expiration controls, according to your organization’s privacy policies, to manage access to your data even after sending.
Right-sized security and data loss prevention controls ensure your emails are protected according to their sensitivity.









“For sharing personally identifiable information, for example, or financial information with contractors, Zivver ensures data is protected. The ability to share large files directly from Microsoft 365 is also very helpful. While compliance wasn’t the main reason for implementing Zivver, it is very important. We can access data and reporting on user activity in the back end, including some interesting statistics regarding data incidents avoided. We can even see when emails have been recalled. This data supports us in meeting compliance.”

James Ryan, Infrastructure Manager
Soha Housing


Whatever you need to know, we’ve got the answers.
With most “secure email” or “secure file sharing” solutions, the service provider has access to the decryption keys because they are stored on the provider’s servers. This makes them vulnerable to insider threats, attractive targets for hackers, and susceptible to government access requests, such as under the CLOUD Act.
Zivver’s zero-knowledge encryption is based on the principle that Zivver itself has no access to the keys needed to decrypt stored information. As a result, Zivver is immune to these risks.
Zivver’s zero-knowledge encryption is designed to meet the strict requirements of various data protection laws, including the GDPR, HIPAA, and ISO standards.
Because only the sender and intended recipient have access to the contents of messages and files, Zivver’s encryption method complies with the core requirement of these laws—to protect sensitive data from access by third parties. Since Zivver does not store decryption keys and therefore cannot provide access to information, the risk of a data breach is greatly reduced, even in the event of a server compromise. This also means that Zivver cannot disclose any data in response to potential government information requests.
No, due to Zivver’s Zero Knowledge Encryption model, Zivver cannot access or recover encrypted data if a user loses access to their encryption keys.
This is because Zivver does not store or have access to these keys. The decryption keys are only accessible to the the sender or the recipient.
While this provides a high level of security and privacy, it also means that it is essential for users to securely manage and back up their decryption keys, as losing them would result in the permanent inability to decrypt the stored information.
12 min read
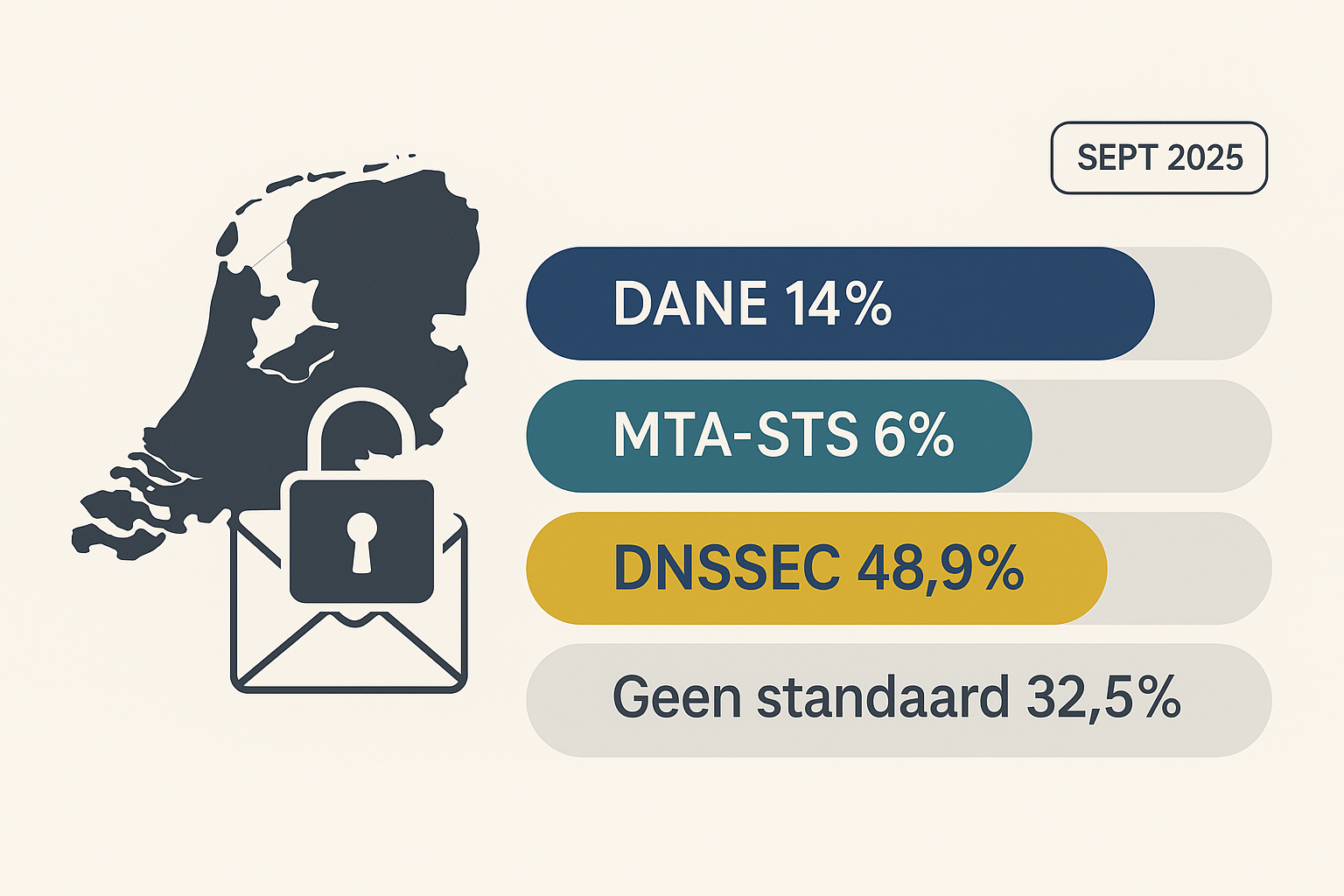
Summary Only 14% of the domains analyzed support DANE, and just 6% support MTA-STS. This means that over 80% of domains still fail to meet the basic standard for secure email transport. One in three d...

min read
Learn how email data loss prevention keeps sensitive information safe.

min read
Hear insights from AI and cybersecurity leaders on how to build cyber resilience through AI powered tools and training.