DORA compliance
Meet DORA email requirements with Zivver.
Get ahead of the upcoming DORA regulatory framework with our effortless email security solutions.
Meet DORA email requirements with Zivver.
Get ahead of the upcoming DORA regulatory framework with our effortless email security solutions.
In January 2025, all financial institutions operating across the EU will be required to comply with the new Digital Operational Resilience Act (DORA), a regulatory framework designed to ensure that organizations are both protected and prepared for potential security incidents.
Through a series of requirements, DORA augments the digital operational resilience of financial entities, effectively ensuring the robustness of the entire financial system.


DORA introduces rules pertaining to the protection, detection, containment, recovery, and repair capabilities against ICT-related incidents. It outlines regulations concerning ICT risk management, incident reporting, operational resilience testing, and ICT third-party risk monitoring.
The regulation defines financial entities in a broad and self-inclusive way. The financial institutions mentioned include, but are not limited to credit institutions, payment institutions, investment firms, and more.
The ‘Protection and prevention’ article in DORA places great importance on the robust security and proper functioning of ICT systems within financial entities to minimize risk. Organizations must adopt ICT security tools, policies, and procedures to ensure the secure transfer of data, minimize the risk of corruption or loss of data, unauthorized access and technical flaws that may hinder business activity.
Organizations must continually monitor tech to prevent the lack of availability, impairment of the authenticity and integrity, breaches of confidentiality and the loss of data, as well as ensuring data is protected against risks arising from data management, including poor administration, processing-related risks, and human error.


Due to a lack of security functionality, email is inherently insecure and poses some great challenges in meeting regulations such as DORA. For example, standard email traffic is not encrypted, making it susceptible to interception and unauthorized access. As a result, email does not guarantee the confidentiality of sensitive data.
In addition, 2FA is a common security measure in many services, it is rarely implemented in email communication, leading to potential unauthorized access and data breaches, and falling short of DORA's stringent security mandates.
Zivver reads the body and attachments of emails to prevent the leading causes of data incidents. Zivver alerts users to potential errors including misuse of Bcc and incorrect recipients, empowering employees to correct mistakes or apply appropriate security measures before sending. Zivver also applies advanced encryption to guarantee that data is protected in transit against potential interceptions and unauthorized access.
We don’t hold client decryption keys, ensuring the total data confidentiality. To prevent unathorized access once an email has been received, users can apply 2FA controls or expiration controls.
Zivver also enables users to recall emails, without limits. So, if a mistake happens, employees can view the status of an email (including whether it has been accessed, forwarded, and by who), and guarantee an incident has been avoided in the instance it is yet to be opened.

There’s no such thing as a silly question. Whatever your ask, we have the answers.








Close the other tabs. Zivver Secure Email platform provides a suite of secure integrations to power productivity.


5 min read
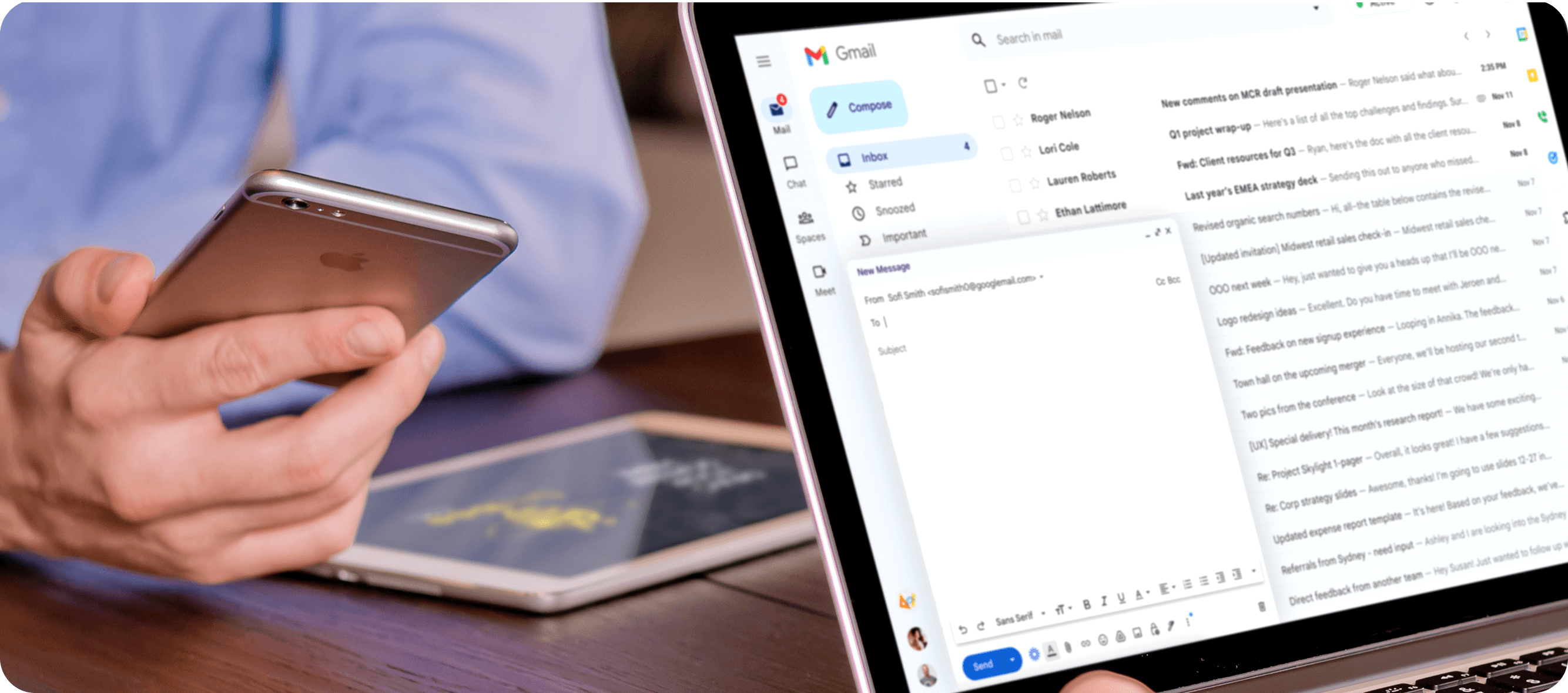
Google Workspace has over 3 billion users globally, while Gmail has over 1.5 billion users per month. That’s almost three times more than its closest competitor, Outlook.

min read
Learn how email data loss prevention keeps sensitive information safe.

min read
CISO, Nadine Hoogerwerf, and Chief Innovation Officer, Dr Rick Goud, explore NIS2, and share practical steps on how organizations can meet compliance.